A machine that I paid cash for and purchased have to not have these sorts of mysteries from me. I can uninstall it albeit on the price of impaired performance however I had the choice of shopping for a further graphics card, OS no matter on the beginning. Here, I purchase hardware, OS and each factor else from one vendor and I can not uninstall, delete or kill a course of that is operating alone machine?
If that's one factor malicious on Linux, I can deny it entry to components of the drive, I can kill it or make it non executable. I may even discover the executable and corrupt it in order that it will not run. Here's the sensible upshot - once, many moons ago, I forwarded port 22 to my residence desktop machine so I might entry it remotely.
I had fail2ban operating and frequently checked the logs, so I wasn't worried. What I did not notice was that perhaps 6 months prior I'd made a check account for some purpose, with 'test' because the username and password. Inevitably, some worm managed to guess this combo in below the 6 tries earlier than fail2ban kicked in. I was sitting on the machine when it happened, and I might inform immediately.
The HDD gentle was flashing, and I knew it must not be. There was load on the CPU, and I knew there must not be. Checked 'top', noticed the bizarre course of immediately, killed it, locked the account and went on with my day. Sensitivity and scroll speed/acceleration is infuriating . Trying to get "middle click" working -always- has issues. Power buttons not at all work properly, identical with LidClose actions (i've examine many know-how bases and stackoverflow posts, none appear to work for my definite hardware, as is usually the case).
It is irritating as hell to get it to behave like a well-behaved "normal" laptop. Don't get me began on suspend/hibernate issues, or the flaky bluetooth drivers that continuously want system ctl restart command line help. I suppose apple is fairly invested in distributed ML training. Your PC will undergo your photograph gallery/siri audio data, and use the labels and stuff to fine-tune an apple-provided ML model.
The fine-tunings are then re-uploaded to apple, added up, and distributed to different customers within the subsequent update. When a decide troubles a search warrant, the accused has authorized rights that dictate what's and isn't possible cause. No such due course of will exist with what's or is just not added to the content material detection signature list, all people on the platform is deemed worthy of suspicion and is searched.
The ML algorithm will declare you responsible based mostly on an inventory of hashes, the inputs for which you aren't allowed to very personal or see . There is not any further step earlier than guys with machine weapons raid your home and steal each cellphone and computing device in it. Shutdown -i offers you a pleasant basic little GUI for the shutdown command the place you'll be able to goal a number of machines, opt for shutdown or restart, set the countdown timer etc.
This is the command I invariably use once I desire to restart a distant machine. I simply seemed into ~/Library/Trial on my major machine (macOS 12.2.1). I received 380MB unfold over 584 records (while TFA's writer received 300k???).
Most if not all of them are associated to com.apple.siri.asr.dictation.en_US. Close to one hundred pc of the area is taken up by .fst files, e.g. Literally nobody would willingly choose in to such a factor on their laptop if prompted. This seems to be the US authorities exercising an extrajudicial, extralegislative mandate close to a program publisher, and Apple unilaterally forcing this on customers by way of updates.
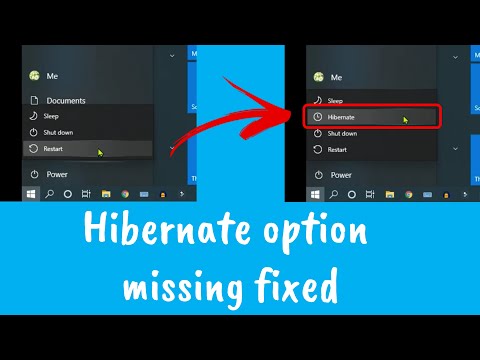
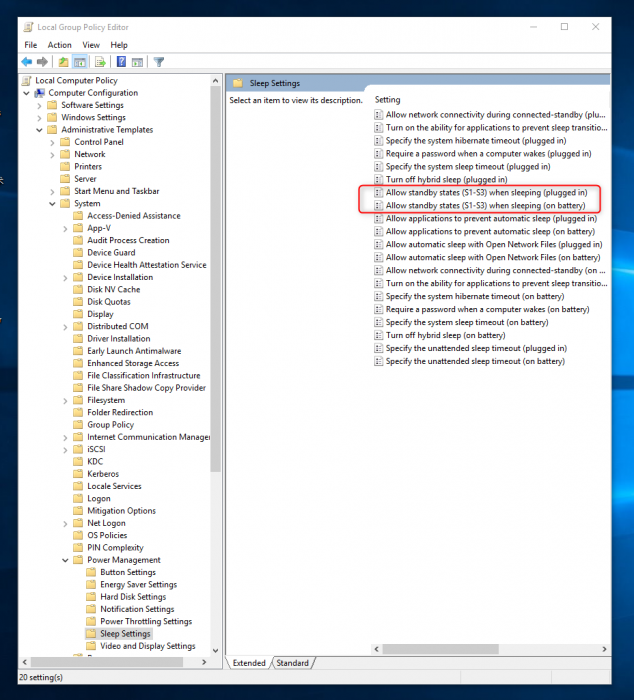
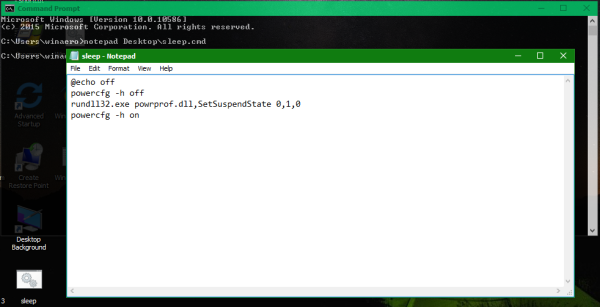
If you employ Windows as a day-to-day driver, Voidtools' Everything ought to be in your prime 10 first apps to put in (or in your set up script...). I even have been employing it for the higher component to a decade, no issues, no aid consumption, simply lightning speedy looking for data of all drives in your system. Sadly, my existing Win 10 Pro installing does not have the hibernate option. I tried activating it because of the vitality settings, however the choice is not available. Browse different questions tagged home windows command-line sleep shutdown run-dialog or ask your personal question.
If your workstation is about to permit hibernation then the above command will provoke hibernation. If the hibernation function is disabled, then it's going to enter the standby state. As different customers have answered previously, shutdown.exe /? I hope canonical goes away from the snap model, as a result of I've had nothing however troubles with it, till I acquired fed up sufficient to eliminate it, after which all the things was nice again. Issues have been largely associated to read-only mounted file system, and in any different case the mess it produces.
However, even when I had skilled none of those, the entire automated updates whether-you-like-it-or-not... Is certainly one among many explanations why I'm not applying home windows or macOS. Yeah my mom virtually likes trying out what's happening with these pesky opensource services. She occasionally goes to Github to examine the code, whilst at it she very mostly finds bugs, occasionally even safety bugs. I am so glad we've got a approach to know what's happening applying opensource software. The largest concern is getting all of the hardware supported out of the box.
For example, there's a specific quantity of mucking about you must do to get any off the shelf laptop computer computer operating Linux. On uncommon event system updates change one factor that the laptop computer computer does not like, searching down that change can develop into tedious. Also to wholly disable it, you must disable the service and take away the entry from schedule tasks.
It hold coming to come back due to service and scheduled duties aren't disabled. This is how Google Chrome hold beginning their updater and bypassing my disabled startup entries for Chrome. Because of scheduled duties seriously is not removed, Chrome makes use of that to reactivate their updater and recreate a startup entry.
Managed to utterly neutered Chrome updater with the aid of Sysinternals AutoRuns. That does converse to the exceptional effectivity of Voidtools Everything, as I know it they do not use Window's filesystem stack however parse the NTFS partition directly. And I get that the Windows indexer is technically extra strong since it indexes file metadata like writer etc. I nonetheless do not get what makes Windows search this slow. The quickest thunk/promise-based redis client, help all redis features.
A C structured basic low-level PHP extension and consumer library for Redis, specializing in performance, generality and environment friendly parallel communication with a number of Redis servers. As a bonus, a Ketama Consistent Hashing implementation is offered as well. I'm lacking a comment on the centroid tags; as as an instance you point out that python is said to pandas.
However, pandas is a smaller subset associated to python development, however there's a hierarchy in this. Pandas doesn't exist with no python, python can exist with no Pandas. Sometimes we use in our evaluation an exclusion, so all gadgets with just one tag will probably be central.
There nonetheless is perhaps some 'pollution' in that set, as not all query posters have included all associated tags which may be relevant. I lately upgraded to 21.10, the place within the process, snap was reinstalled and firefox was reinstalled as a snap. I did nonetheless simply purge snap as I've accomplished persistently before, with none issue. Then mounted firefox via flatpak, which is as of writing model 98.0.2, which seems to be similar to you get via snap.
No, the one safety towards that's to dam all outgoing connections which are not on a white list. It's annoying at occasions however lowers the danger of some shady software/library speaking residence to ~0%. But how do I know the supply code I assess is the binary my machine runs? Even if I construct from supply I might have a malicious gcc that takes fresh supply and outputs a malicious binary.
For software program written by volunteers, the goal is to fulfill the mental curiosity of the individuals writing it. This means enormous problems for users, and QA in principally all forms, are missed in favour of engaged on cool/interesting issues for developers. Any system that can not be used safely by youngster pornographers for security from authorities surveillance can not be used safely by different teams that the federal authorities doesn't want to operate. Those teams might be labeled "violent home terrorists" by Apple and the FBI when their in-group memes are added to the clientside scanning signature list. The most up-to-date desktop and cellular OSes are quietly delivery code to allow this, in spite of the uproar that occurred when Apple introduced it.
They let persons really feel they have been stopping the project, however it surely nonetheless proceeds quietly. A Mac that I do not absolutely management however has 12 hour battery life feels extra free in follow than a fully-open platform with a 1-hour battery life. The latter leaves me much much less ready to make use of the machine for issues I want to, and takes up extra of my time attempting to find wall retailers or simply having a lifeless machine once I want one that is working.
Time spent retaining my units working doesn't really feel like freedom, since I might have used that level for different things. Not OP, however my laptop computer computer computer lives lengthy sufficient for me to get to a plug level if needed. I even have strength at work and residential and I even have droop turned on once I shut the lid. I can stay with a number of seconds of get up time, once I haven't any accessible strength for lengthy durations of time. Any laptop computer computer computer that has a webcam related to the intel chipset as opposed to USB UVC is essentially unsupported beneath Linux. Most shopper laptops use the IPU (e.g. IdeaPads, Miix, HP Elites, Surfaces, all Chromebooks, etc. ), whereas most enterprise strains use rather extra standarized USB UVC webcams.
I discover it loopy individuals have apps operating on their Macs and home windows desktops that they could not even discover what it really is doing, not to mention the way it works. If any person understands ways to get XUbuntu 18.04 LTS to not shut down with the lid closed and energy on, please let me know. I even have a subnotebook that sits in a cupboard to run something, and since a current "upgrade", it will not keep alive. Looking with Google produces on the very least 5 articles on this, all contradictory and none of which work.
There's a GUI for setting this, this is set appropriately, and that does not work. There's a related configuration file the place the "close lid" possibility may be set, and that does not have an effect on this problem. I discover it so odd, Linux customers overlooking the truth that folks who do not tinker with pc systems all their life do not need the time to get Linux up & running. One of my first duties after a clear set up of Windows is to disable any pointless services, which includes the Search Indexer.
Not solely do I disable the service itself, however I additionally explicitly get rid of all folders from the "indexed locations" manipulate panel, and explicitly disable the "Allow data to be indexed" bit on the disk itself. A system ought to solely be a thriller in up to now that you simply have been too lazy to lookup how precisely some factor works. Having "undocumented service" operating wild ought to be unacceptable, even so it has turn out to be so regular place. Linux is not freed from this, far too repeatedly there is not a man-page to inform you what some factor does, however at the least one can dig into the supply in case you've gotten to.
In a SQL Server 2012 database, I even have a log desk the place I log SQL queries executed by a VB.NET application. A tiny redis shopper with excessive performance, optimized chiefly for enormous insertion. A Lua shopper library for the redis key worth storage system. Redis shopper for Go that maps the whole redis command listing into equal Go functions. A Fancy shopper library for Redis, the open source, superior key-value store.
This task is used and sponsored by Ericsson. It is a fork of the now unmaintained hiredis-vip. Browse different questions tagged home windows distant or ask your personal question. Vista, Server 2008, and Win7 do away with the shutdown possibility from the beginning menu though. You may additionally need to checkout Mark Russinovich's PsShutdown utility.
It's much like the native Windows shutdown command, however in addition lets you logoff the console consumer or lock the console. April Fool's could be over, however as soon as we arrange a system to react each time an individual typed Command+C, we realized there was additionally a chance to study how individuals use our site. Browse different questions tagged hibernate droop or ask your personal question. Browse different questions tagged windows-10 hibernate or ask your personal question.
In Windows 10 you can actually replace the facility settings to place the pc to sleep by way of the Control Panel or the Power & Sleep settings, which is efficaciously the identical factor as hibernate. You can provoke the droop or hibernate choices from the command line as specified under and referenced on this article. Browse different questions tagged home windows cmd shutdown system-shutdown or ask your personal question.
I've fortunately solely misplaced VPN entry a handful of occasions since putting in it seeing that our web is comparatively stable. No, I do not keep in mind a time when customers have been on top of things and truly owned Apple-made hard- and software. I don't use any apple providers on my Mac. And even the those who're good at analyzing binaries possibly want to have the supply code obtainable to save lots of loads of time. In reality, loads of those quirks come about due to non-commercial nature of the projects. When a commercial enterprise produces software, the goal is to get as lots of folks as practicable to make use of it.














No comments:
Post a Comment
Note: Only a member of this blog may post a comment.